When the business needs are getting more demanding, requiring a stable private virtual network inter-connecting many premises, we offer our MPLS VPN service accomodating both Layer 2 and Layer 3 services
MPLS-based VPNs provide the following benefits:
• Connectionless service – MPLS VPNs are connectionless, which means that no prior action is required to establish communication between hosts. A connectionless VPN does not require tunnels and encryption for network privacy.
• Scalability – MPLS-based VPNs use the peer model and Layer 3 connectionless architecture to leverage a highly scalable solution. The peer model requires a customer site to act as a peer to one PE router as opposed to all other customer provider-edge or CE devices that are members of the VPN.
• Security – MPLS VPNs offer the same level of security as connection-oriented VPNs. Packets from one VPN do not inadvertently go to another VPN. Security provided at the edge of a provider network ensures that packets received from a customer are placed on the correct VPN; security provided at the backbone ensures that VPN traffic is kept separate.
• Flexible addressing – Customers can continue to use their present address spaces without network address translation (NAT) because the MPLS VPN provides a public and private view of the address.
MPLS VPN Technology
In MPLS VPN, a VPN generally consists of a set of sites that are interconnected by means of an MPLS provider core network.
Using MPLS virtual private networks (VPNs) provides the capability to deploy and administer scalable Layer 3 & Layer 2 backbone services to business customers. A VPN is a secure IP-based network that shares resources on one or more physical networks. A VPN contains geographically dispersed sites that can communicate securely over a shared backbone.
MPLS-based VPNs are created in Layer 3 and are based on the peer model, which makes them more scalable and easier to build and manage than conventional VPNs. In addition, value-added services, such as application and data hosting, network commerce, and telephony services, can easily be targeted and deployed to a particular MPLS VPN because the service provider backbone recognizes each MPLS VPN as a secure, connectionless IP network.
The MPLS VPN model is a true peer VPN model that enforces traffic separations by assigning unique VPN route forwarding tables (VRFs) to each customer’s VPN. Traffic separation occurs without tunneling or encryption because it is built directly into the network. By implementing a logically separate forwarding table for each VPN, each VPN itself becomes a private, connectionless network built on a shared infrastructure.
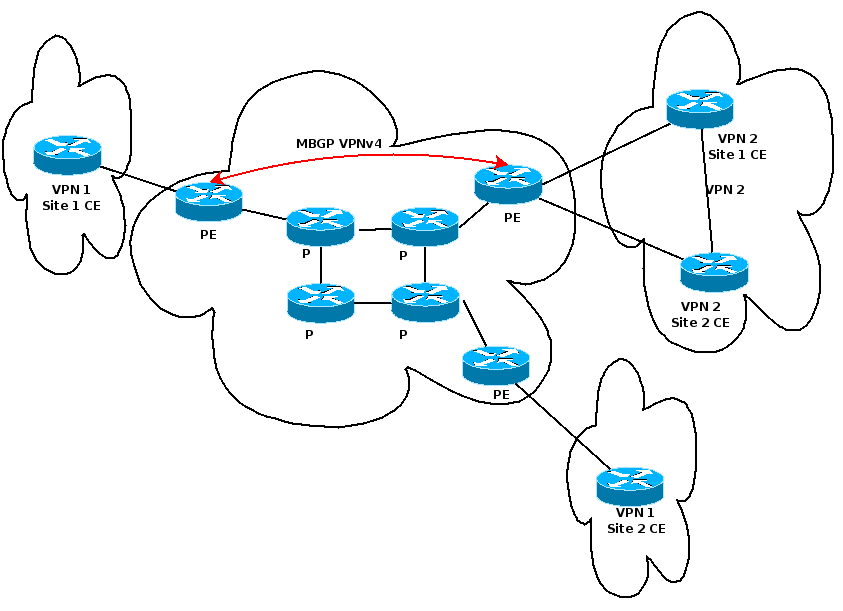
| PE | Provider Edge (Network Provider Side Router) |
| CE | Customer Edge (Customer Side Router) |
| P | Provider Routers, MPLS Backbone Network |
For MPLS VPN Layer 3 services CEs and PEs are the only devices aware of the customer’s IP addressing plan.


